Lab 7: Baseline Configuration
Scenario
Many organizations standardize server configurations by applying their group policies and hardening rules to reduce risks caused by misconfiguration. Taking Windows Server as an example, it is very common to apply default firewall rules, disabled services, custom registry values, and user & role permission settings. You’ll learn how to use Automation Config to automate baseline configuration for Windows Server.
Task A. Enable Remote Desktop Service (RDS)
- Click Configurations > File Server from the side menu
- Expand base folder in the file server folder tree
- Locate
/POV/config-management/windows/base-config/enable_rds.sls - Click
enable_rds.slsand examine its SaltStack State File YAML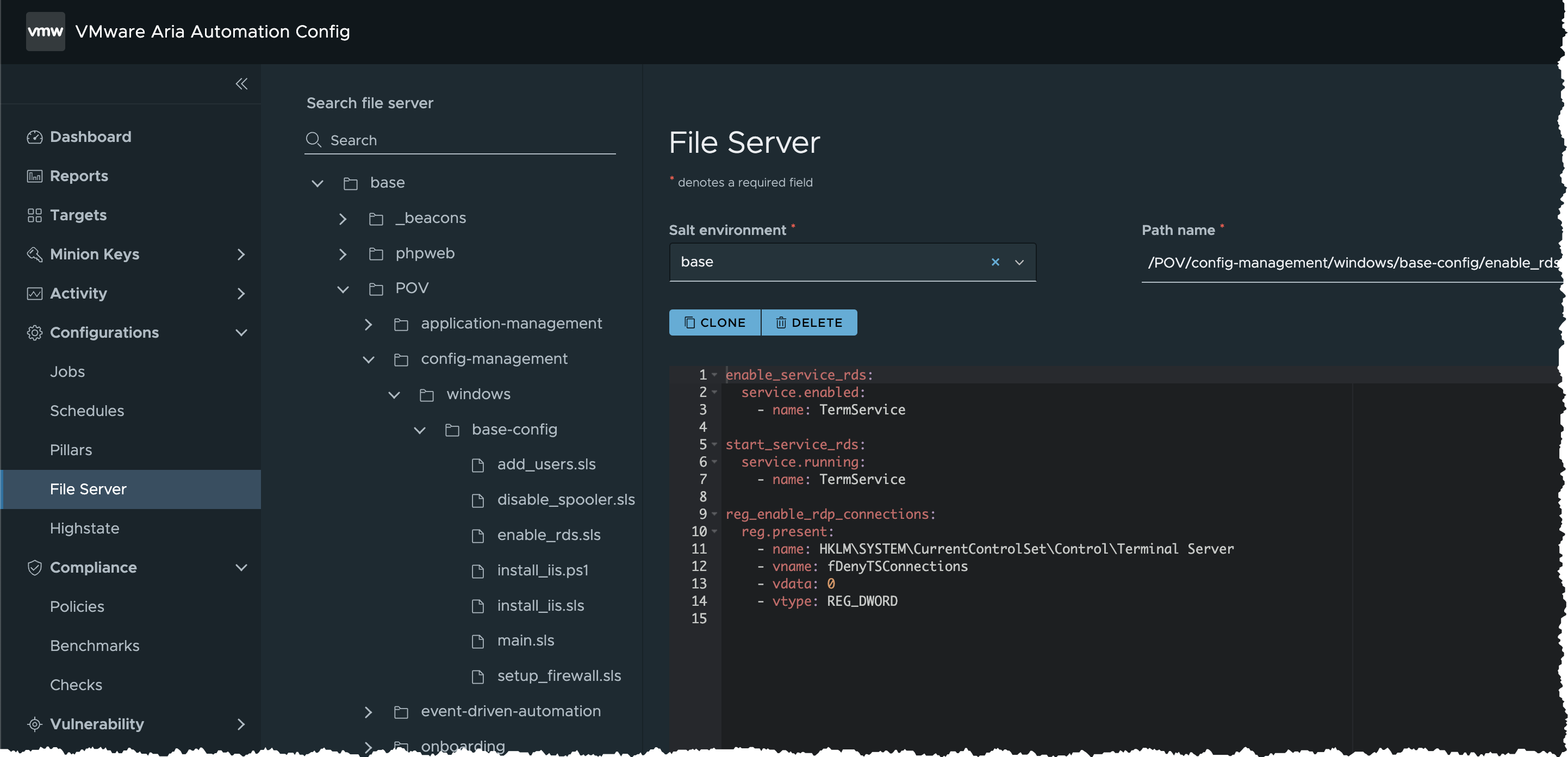
enable_service_rds: service.enabled: - name: TermService start_service_rds: service.running: - name: TermService reg_enable_rdp_connections: reg.present: - name: HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server - vname: fDenyTSConnections - vdata: 0 - vtype: REG_DWORD - Running this state file will enable
Remote Desktop Service (RDS)on the target minions, but we are NOT going to run it now. We will apply this state collectively as a baseline configuration
Task B. Disable Printer Spooler Service
- Click Configurations > File Server from the side menu
- Expand base folder in the file server folder tree
- Locate
/POV/config-management/windows/base-config/disable_spooler.sls - Click
disable_spooler.slsand examine its SaltStack State File YAMLdisable_print_spooler: service.disabled: - name: Spooler stop_print_spooler: service.dead: - name: Spooler - Running this state file will disable
Printer Spooler Serviceon the target minions, but we are NOT going to run it now. We will apply this state collectively as a baseline configuration
Task C. Install IIS Web Server
- Click Configurations > File Server from the side menu
- Expand base folder in the file server folder tree
- Locate
/POV/config-management/windows/base-config/install_iis.sls - Click
install_iis.slsand examine its SaltStack State File YAMLinstall_iis: cmd.powershell: - name: salt://POV/config-management/windows/base-config/install_iis.ps1 - As you can see, the state file is refering to a PowerShell script in the File Server
- Locate
/POV/config-management/windows/base-config/install_iis.ps1 - Click
install_iis.ps1and examine this regular PowerShell scriptInstall-WindowsFeature -name Web-Server -IncludeManagementTools - Running this state file will execute the PowerShell script to install IIS web server on the target minions, but we are NOT going to run it now. We will apply this state collectively as a baseline configuration
Task D. Setup Firewall Rules
- Click Configurations > File Server from the side menu
- Expand base folder in the file server folder tree
- Locate
/POV/config-management/windows/base-config/setup_firewall.sls - Click
setup_firewall.slsand examine its SaltStack State File YAMLopen_smb_port: win_firewall.add_rule: - name: SMB (445) - localport: 445 - protocol: tcp - action: allow open_http_port: win_firewall.add_rule: - name: HTTP (80) - localport: 80 - protocol: tcp - action: allow open_https_port: win_firewall.add_rule: - name: HTTPS (443) - localport: 443 - protocol: tcp - action: allow - Running this state file will add three firewall rules on the target minions top allow incoming SMB, HTTP & HTTPS connection, but we are NOT going to run it now. We will apply this state collectively as a baseline configuration
Task E. Add Default Users
- Click Configurations > File Server from the side menu
- Expand base folder in the file server folder tree
- Locate
/POV/config-management/windows/base-config/add_users.sls - Click
add_users.slsand examine its SaltStack State File YAMLadd_user: user.present: - name: holuser - fullname: holuser - password: VMware1! - groups: - Administrators - Users - Running this state file will add
holuseruser toAdministratorsandUsersgroups in the target minions, but we are NOT going to run it now. We will apply this state collectively as a baseline configuration
Task F. Create Baseline Configuration
- Click Configurations > File Server from the side menu
- Expand base folder in the file server folder tree
- Locate
/POV/config-management/windows/base-config/main.sls - Click
main.slsand examine its SaltStack State File YAMLinclude: - pov.config-management.windows.base-config.enable_rds.sls - pov.config-management.windows.base-config.disable_spooler_service.sls - pov.config-management.windows.base-config.install_iis.sls - pov.config-management.windows.base-config.setup_firewall.sls - pov.config-management.windows.base-config.add_users.sls - Running this state file will apply all above states collectively as a baseline configuration
- Next, we will create a job to run this state file
Task G. Create Job - Baseline Configuration
- Click Configurations > Jobs in the side menu
- Click Create Job button
- Input the following details for the new job and save the job
- Name =
Baseline Configuration for Windows - Description =
Baseline config: RDS, IIS, Firewall & Users, etc. - Command =
salt - Targets =
Windows Servers - Function =
state.apply - Environments =
base - States =
POV.config-management.windows.base-config.main - Arguments = (Blank)
- Job Inputs = (Blank)
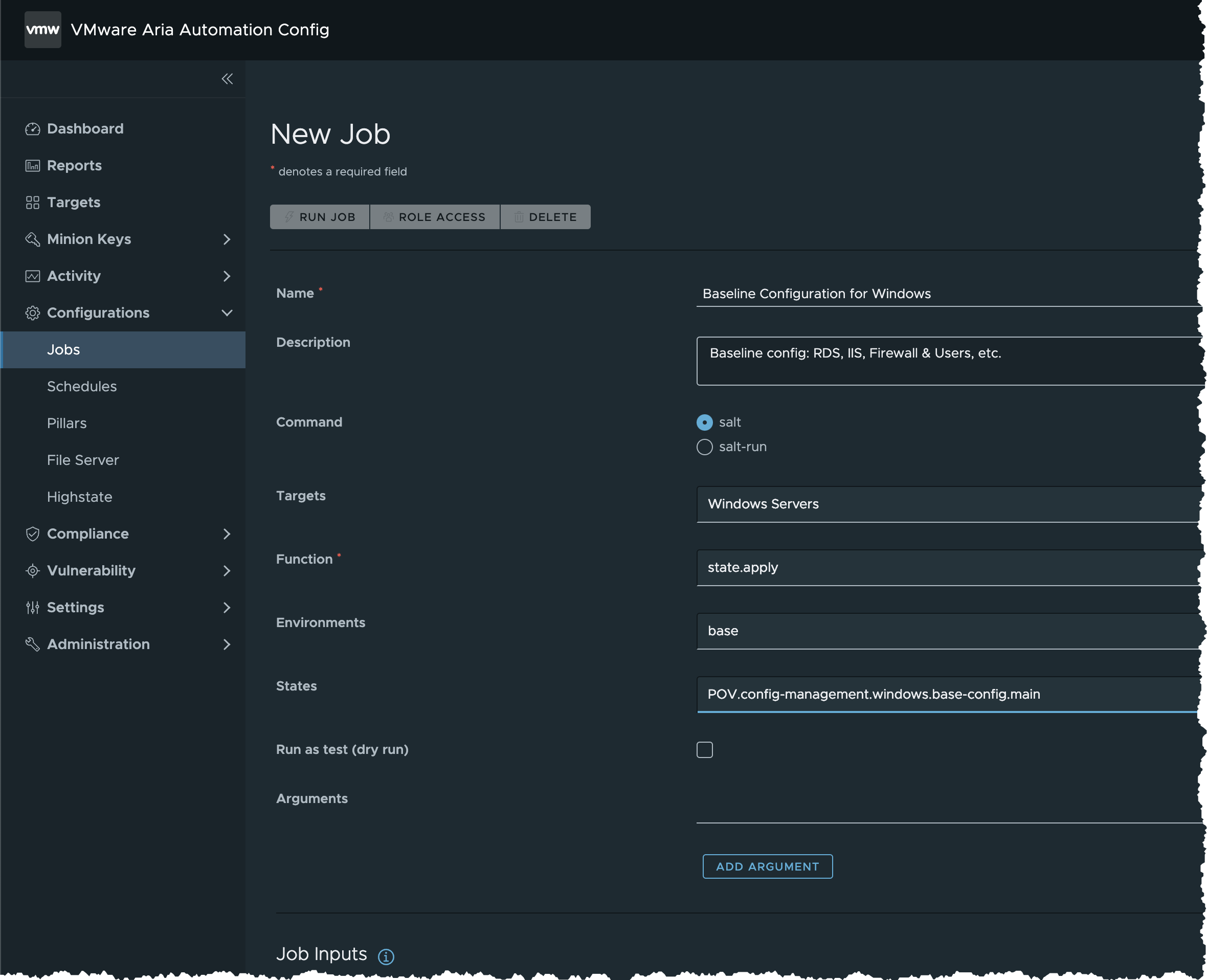
- Name =
- Click SAVE button
- Now that you’ve created a job
Task H. Run Job - Baseline Configuration
- In the side menu, click Targets to open the Targets workspace and view your targets
- Locate Windows Servers minions target
- Click the button besides Windows Servers and select Run job
- In the Run Job dialog box
- Input the following details
- Job =
Baseline Configuration for Windows(the job you have created in the previous task) - States = (Unchanged)
- Run as Test =
false - Environments =
base - Options = (Unchanged)
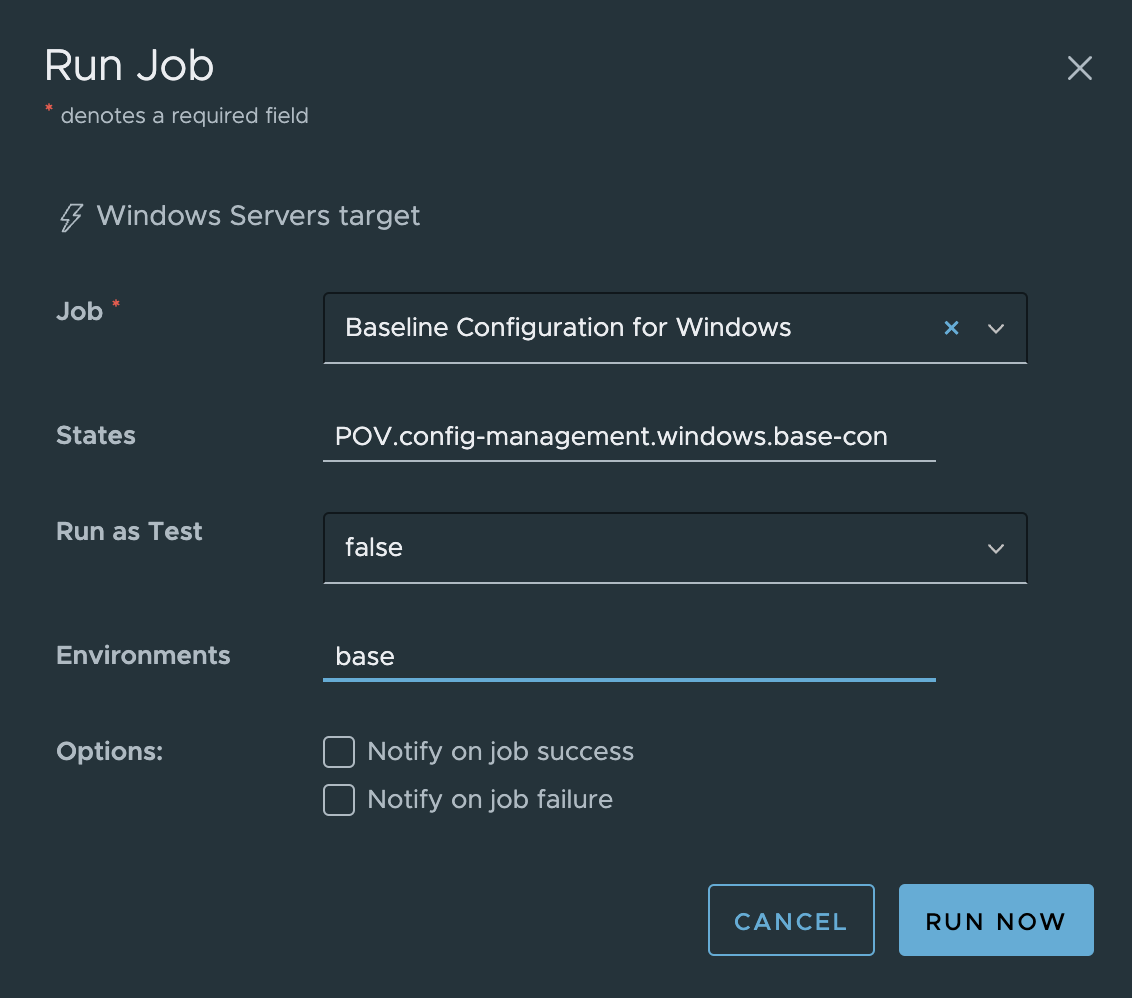
- Job =
- Input the following details
- Click RUN NOW button
- Click Activity > Completed in the side menu
- The job will appear on the list once it is done. If not, Refresh the page in your browser
- Check if this job is completed successfully without error
- Check Success is 1 or higher, and Failed is 0
Task I. Check Results - Baseline Configuration
- Log on to one of the target Windows minions
- Check if Remote Desktop Service (RDS) service is enabled
- Check if Printer Spooler service is disabled
- Check if IIS Web Server is installed
- Check if Firewall rules are configured to allow SMB, HTTP & HTTPS
- Check if User
holuseris created
Summary
Automation Config provides various flexible ways to apply baseline configuration:
- Common examples include configuration files, default firewall rules, enabled or disabled services, custom registry values, and user & role permission settings
- Configuration can be applied via Run Command or Run Job
- Configuration State Files can be modularized and stacked when used
- Jobs can be scheduled to run automatically
- Operating System commands, PowerShell and SaltStack functions are supported
- Servers could be effectively managed by grouping into custom group of Minions by using Target Management
- Targets could be securely managed with fine-grained Role-based Access Control (RBAC)
- Baseline configuration is not just for Windows. In the next lab, baseline configuration for Linux will be covered together with automatic drift remediation